Cybersecurity Master's Degree
Continue to main content
Outcomes & Careers
-
$188k
Computer & Information Systems Manager
According to the Bureau of Labor Statistics, the mean annual salary for a computer and information systems manager is $187,990
-
$112k
Computer Systems Analyst
According to the Bureau of Labor Statistics, the mean annual salary for a computer systems analyst is $111,960.
-
$152k
Computer & Information Research Scientist
According to the Bureau of Labor Statistics, the mean annual salary for a computer and information research scientist is $152,310.
With a Master’s degree in Cybersecurity, prepare to enter the field even without a Bachelor’s degree in cybersecurity or similar degree. The program trains new graduates as well as existing practitioners, with skills required to protect critical infrastructure. Take courses in computational cryptography, introduction of cybersecurity, information security in system administration, and security of critical infrastructure.
In addition to the criteria established for general admission to graduate studies, applicants must have the following:
- A bachelor’s degree in cybersecurity or related field*
* Students with bachelor’s degrees from other fields will be required to take up to two prerequisites related to Fundamentals of Computing and Programming. - An undergraduate GPA of 3.0 on a 4.0 scale
- Six completed hours of science and six completed hours of mathematics in the undergraduate degree
Probationary Admission
Applicants who do not meet the general and/or program’s admission requirements may be considered for probationary admission upon approval by the graduate program coordinator. While under probation, students must complete nine credit hours that count toward the degree with a grade of “B” or better to continue in the program.
Core Requirements:
- CY501 Introduction to Cybersecurity (3)
- CY510 Information Security and Assurance (3)
- CY520 Information Security in System Administration (3)
- CY530 Computer Network Security and Defense (3)
- CY620 Advanced Computer Forensics (3)
Choose one thesis option:
Thesis option
- CY655 Research Methods in Cybersecurity (3)
- CY691 Thesis Research I (3)
- CY692 Thesis Research II (3)
- GR699 Master's Oral Examination (0)
- Choose 6 hours of electives from the elective list. At least 3 hours must be at 600 level. (6)
Non Thesis option
- CY690 Graduate Project (3)
- GR698 Master's Final Comprehensive Examination (0)
- Choose 15 hours from the elective list. At least 12 hours must be at the 600 level. (15)
Electives may be chosen from the following with the advice of the advisor:*
- CS506 Distributed Cloud Computing (3)
- CS6xx Computer Science 600 level (except CS605 & CS690) (3)
- CY610 Web Application Security (3)
- CY643 Independent Study (3)*
- CY650 Legal, Risk & Compliance for Security (3)
- CY653 Special Topics in Cybersecurity (3)*
- CY660 Cyber Operations (3)
- CY662 Ethical Hacking (3)
- CY670 Secure Operating Environments (3)
- CS699 Internship (3)*
- MA510 Mathematical Foundations (3)
- MA664 Computational Cryptography (3)
- TN562 Introduction to Networks (3)
- TN564 Routing and Switching Essentials (3)
*May be taken once for credit on the program
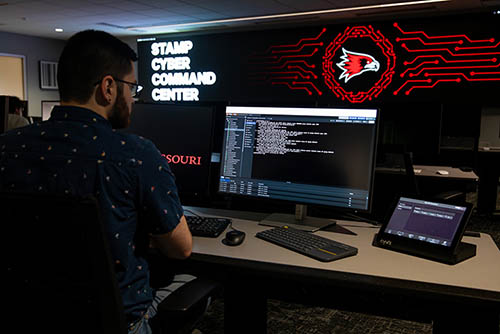
Stamp Cyber Command Center
Get experience-driven, real-world cyber-attack scenarios in the first Cyber Command Center west of the Mississippi. Through SEMO's collaboration with IBM, experience immersive simulations that replicate real-world cyber threats, equipping you with the skills and expertise needed to respond to the evolving cybercrime landscape.
Graduate Assistantships
The graduate assistantship (GA) is designed to provide support during full-time graduate study. It’s an opportunity for the graduate students to serve in a professional role while establishing a professional relationship with faculty and administrators. In addition to a per year stipend, GAs gain valuable experience. There are two kinds of assistantships: teaching and administrative.
Harrison College of Business & Computing
This program is housed in the Harrison College of Business and Computing. The College prepares students for the global marketplace. Alumni work for some of the world’s largest corporations to some of today’s most innovative startups. The focus is on creating and innovating, data and trends, supported by faculty mentors who themselves are leaders in business and computing.
What will it cost?
Getting the Job
Your education is just one piece to launching an extraordinary career. Once you’ve mastered the material, you still have to find the job you want, make the right connections, and sell your knowledge and experience—if all this is giving you anxiety, don’t panic. SEMO’s Career Services office is here to help you with the next step. Our boldly supportive faculty will provide the expertise and support you need, so you’re landing your dream job in no time.
Become a Redhawk.
Do more than dream about the future. Take the first steps to make it all happen.
Graduate Coordinators
Graduate coordinators serve as the contact for graduate programs. The coordinators are most often faculty within the college which houses the program, helping you to get questions answered and first-hand knowledge of the degree requirements and placement opportunities.
Cape Girardeau, MO 63701